Understanding the Global Landscape of DDoS Attacks: A Comprehensive Guide to Live DDoS Attack Maps
Related Articles: Understanding the Global Landscape of DDoS Attacks: A Comprehensive Guide to Live DDoS Attack Maps
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Understanding the Global Landscape of DDoS Attacks: A Comprehensive Guide to Live DDoS Attack Maps. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Understanding the Global Landscape of DDoS Attacks: A Comprehensive Guide to Live DDoS Attack Maps

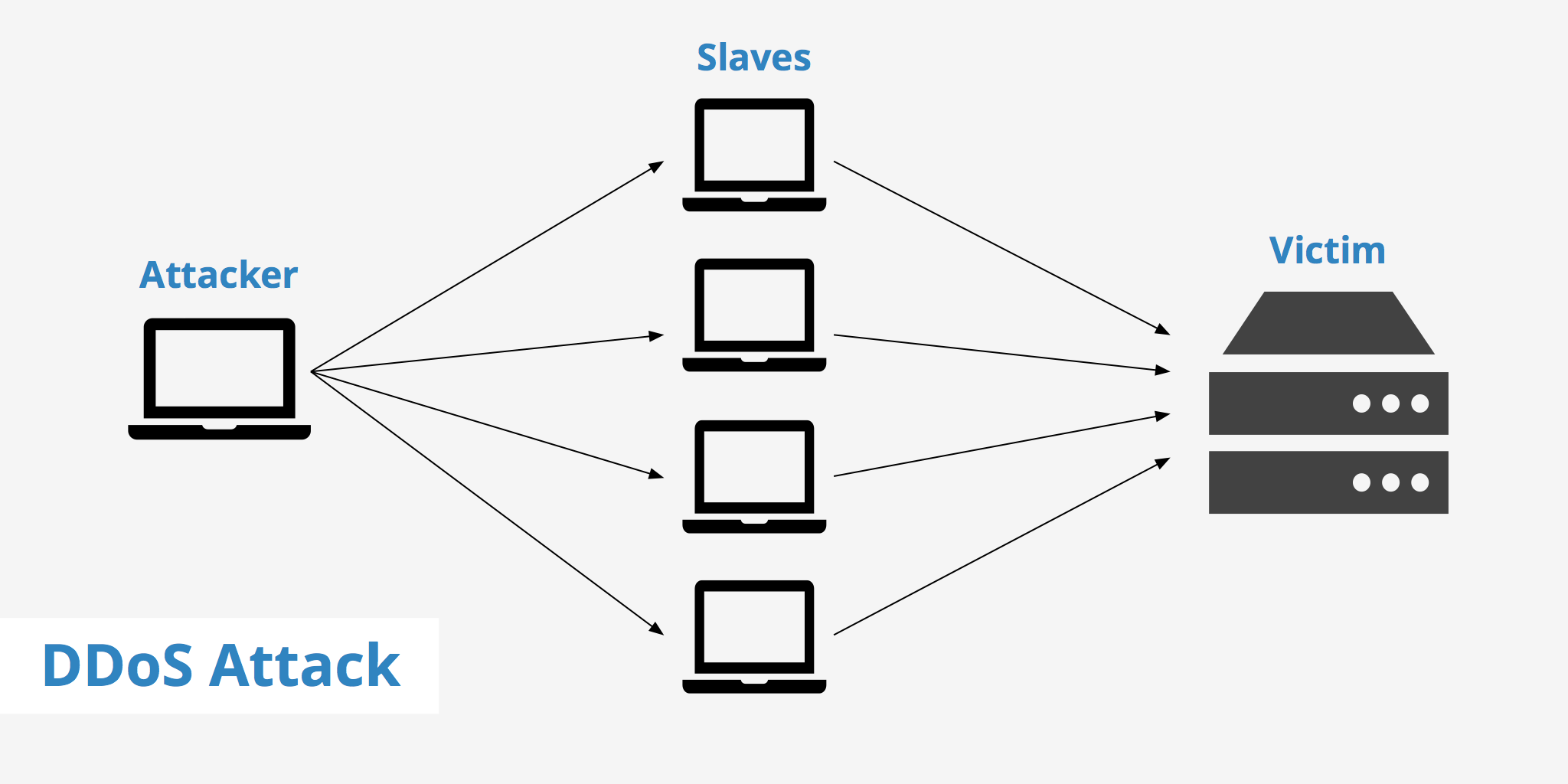
The digital world is a complex and interconnected ecosystem, vulnerable to various cyber threats. Among these, Distributed Denial of Service (DDoS) attacks pose a significant threat to businesses, organizations, and individuals alike. DDoS attacks aim to disrupt online services by overwhelming target servers with a deluge of traffic, rendering them inaccessible to legitimate users. Understanding the global landscape of these attacks is crucial for mitigating risks and ensuring the stability of digital infrastructure. This comprehensive guide delves into the intricacies of live DDoS attack maps, their significance, and how they contribute to a safer online environment.
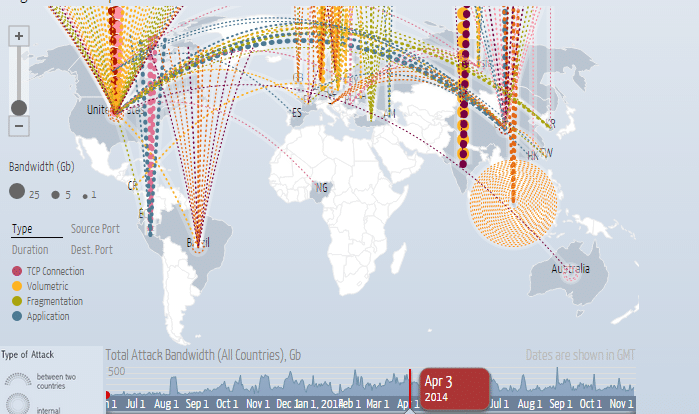
What are Live DDoS Attack Maps?
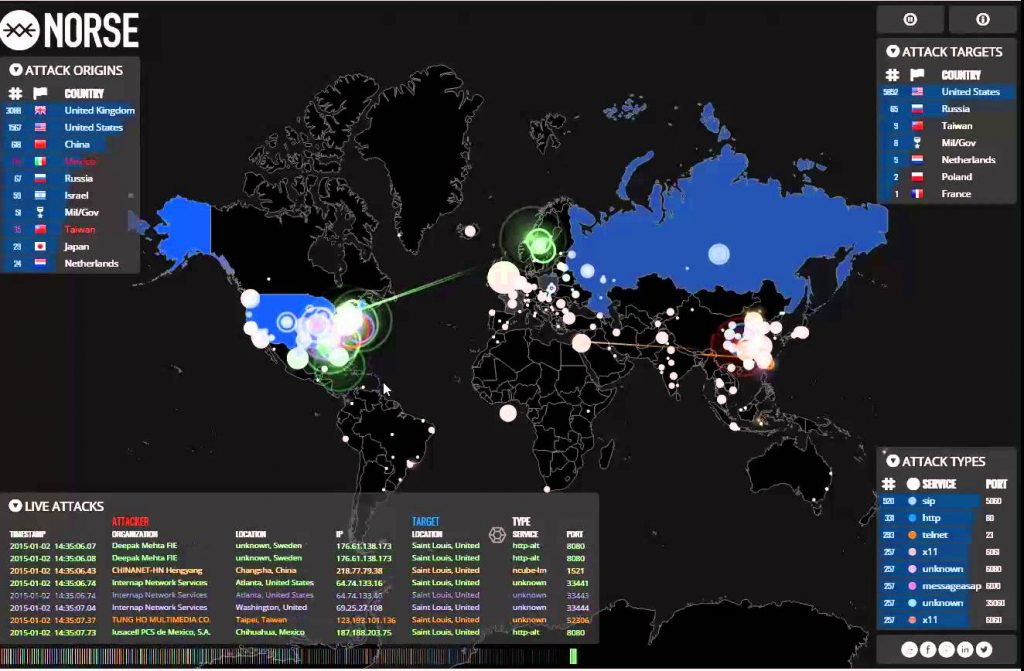
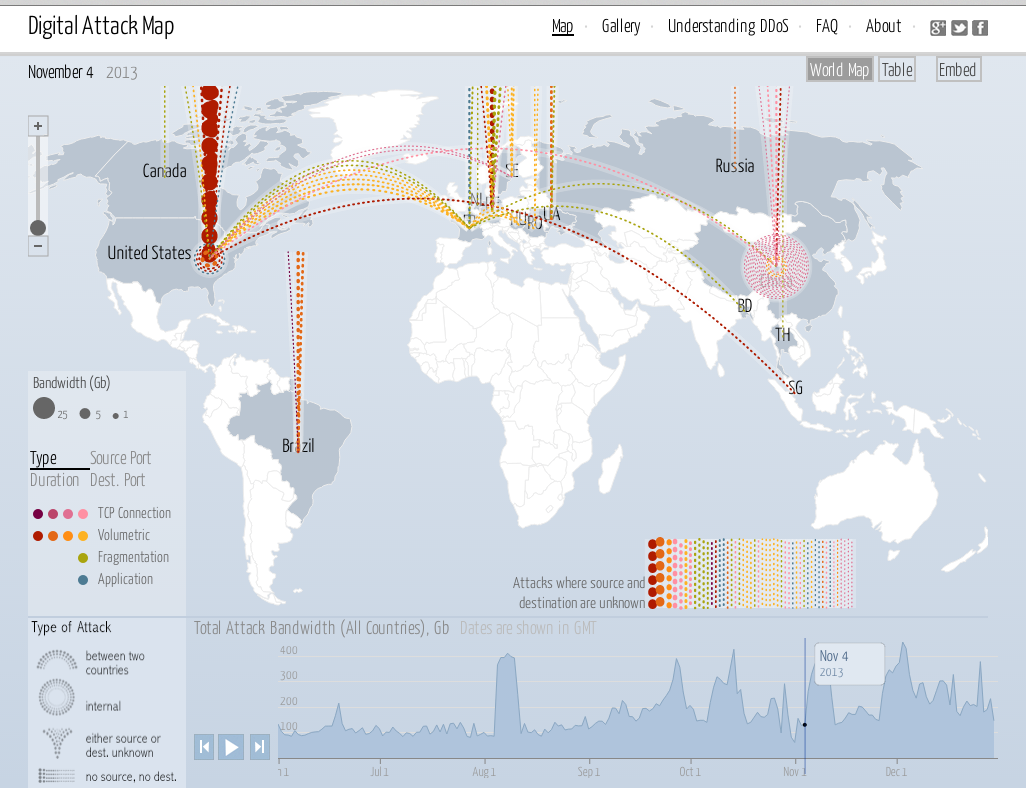
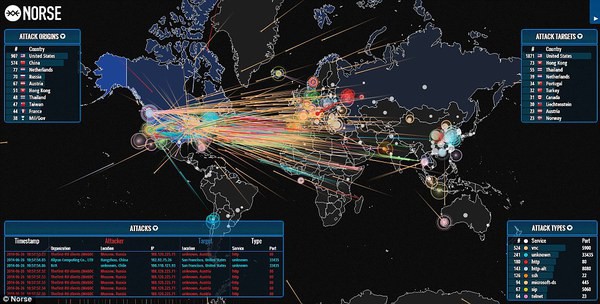
Live DDoS attack maps are dynamic visualizations that provide real-time insights into ongoing DDoS attacks across the globe. They act as visual representations of the global cyber security landscape, offering valuable data on the frequency, location, and severity of DDoS attacks. These maps are typically developed by cybersecurity companies, research organizations, and government agencies, utilizing data gathered from various sources, including:
- Network monitoring systems: These systems collect data on network traffic patterns, identifying anomalies that could indicate a DDoS attack.
- Security information and event management (SIEM) systems: SIEMs analyze security logs and events, detecting suspicious activity and identifying potential DDoS attacks.
- Threat intelligence feeds: These feeds provide real-time information on known DDoS attack vectors, allowing for proactive mitigation strategies.
Benefits of Live DDoS Attack Maps:
Live DDoS attack maps offer several benefits to various stakeholders, including:
- Enhanced Situational Awareness: These maps provide a comprehensive overview of the global DDoS attack landscape, enabling organizations to stay informed about emerging threats and potential vulnerabilities.
- Proactive Security Measures: By visualizing attack patterns, organizations can identify potential targets and implement preventative measures, strengthening their cybersecurity posture.
- Improved Incident Response: Real-time data on DDoS attacks allows for faster and more efficient incident response, minimizing downtime and mitigating potential damage.
- Research and Analysis: Attack maps serve as valuable tools for researchers and analysts, providing data for studying attack trends, identifying attacker motives, and developing effective countermeasures.
Key Features of Live DDoS Attack Maps:
While the specific features of live DDoS attack maps may vary depending on the provider, several common elements contribute to their effectiveness:
- Real-time Data: The maps display live data, providing an up-to-the-minute understanding of ongoing attacks.
- Geographic Visualization: Attacks are typically displayed on a world map, allowing users to visualize attack locations and patterns.
- Attack Type and Severity: Maps often classify attacks by type (e.g., volumetric, application layer, DNS amplification) and severity, providing insights into the nature and impact of attacks.
- Target Information: Some maps may display information about the targets of DDoS attacks, including their industry, size, and geographic location.
- Attacker Information: In some cases, maps may provide limited information about the attackers, such as their location or suspected affiliations.
How Live DDoS Attack Maps Work:
The underlying technology behind live DDoS attack maps involves a complex interplay of data collection, analysis, and visualization. Here’s a simplified overview:
- Data Collection: DDoS attack maps rely on various sources for data, including network monitoring systems, SIEMs, and threat intelligence feeds.
- Data Analysis: The collected data is analyzed to identify patterns and anomalies that indicate DDoS attacks.
- Visualization: The analyzed data is then transformed into a visual representation on a map, highlighting attack locations, types, and severity.
- Real-time Updates: The maps are constantly updated with new data, ensuring that users have access to the most current information.
Examples of Live DDoS Attack Maps:
Several reputable organizations provide live DDoS attack maps, each with its own unique features and data sources. Some prominent examples include:
- Akamai: Known for its content delivery network (CDN), Akamai offers a live DDoS attack map that provides insights into attack trends and global distribution.
- Cloudflare: A leading cybersecurity company, Cloudflare’s DDoS attack map showcases real-time data on attack locations, types, and severity.
- Netlab: A research organization focused on cybersecurity, Netlab provides a live DDoS attack map that offers detailed insights into attack patterns and attacker tactics.
FAQs About Live DDoS Attack Maps:
Q: Are live DDoS attack maps accurate?
A: The accuracy of live DDoS attack maps depends on the data sources used and the analysis methods employed. While these maps provide valuable insights, it’s essential to remember that they are based on a snapshot of the global cyber landscape, and the information may not always be complete or perfectly accurate.
Q: How can I use live DDoS attack maps to protect my organization?
A: Live DDoS attack maps can be a valuable tool for proactive security planning. By understanding attack trends and patterns, organizations can identify potential vulnerabilities and implement preventative measures, such as:
- Strengthening network security: Implementing robust firewall configurations, intrusion detection systems (IDS), and intrusion prevention systems (IPS) can help mitigate DDoS attacks.
- Employing DDoS mitigation services: Organizations can leverage third-party DDoS mitigation services to protect against attacks and ensure service availability.
- Conducting security audits: Regular security audits can help identify vulnerabilities and weaknesses that could be exploited by attackers.
Q: Are live DDoS attack maps a substitute for other security measures?
A: Live DDoS attack maps should not be considered a replacement for comprehensive cybersecurity practices. They provide valuable insights but are only one piece of the puzzle. Organizations need to implement a multi-layered security approach, including network security, application security, and user awareness training, to effectively protect against DDoS attacks.
Tips for Using Live DDoS Attack Maps Effectively:
- Choose reputable providers: Select live DDoS attack maps from trusted cybersecurity companies or research organizations.
- Understand the data sources: Familiarize yourself with the data sources used by the map provider to assess the reliability of the information.
- Analyze attack trends: Use the maps to identify emerging attack patterns and potential vulnerabilities.
- Develop mitigation strategies: Based on the insights gained from the maps, develop proactive security measures to mitigate DDoS attacks.
- Stay informed: Regularly monitor live DDoS attack maps to stay updated on the latest attack trends and threats.
Conclusion:
Live DDoS attack maps are powerful tools that provide valuable insights into the global landscape of DDoS attacks. By visualizing real-time data on attack locations, types, and severity, these maps empower organizations to enhance their situational awareness, implement proactive security measures, improve incident response, and contribute to a safer online environment. While these maps are not a substitute for comprehensive cybersecurity practices, they serve as a valuable resource for staying informed about emerging threats and developing effective mitigation strategies. As the digital world continues to evolve, live DDoS attack maps will play an increasingly important role in safeguarding the integrity and stability of online services.


Closure
Thus, we hope this article has provided valuable insights into Understanding the Global Landscape of DDoS Attacks: A Comprehensive Guide to Live DDoS Attack Maps. We appreciate your attention to our article. See you in our next article!